Joomla! Debug Console
- The database row is empty.
| Call stack |
| # | Function | Location |
|---|
| 1 | JSite->dispatch() | JROOT/index.php:42 |
| 2 | JComponentHelper::renderComponent() | JROOT/includes/application.php:194 |
| 3 | JComponentHelper::executeComponent() | JROOT/libraries/joomla/application/component/helper.php:348 |
| 4 | require_once() | JROOT/libraries/joomla/application/component/helper.php:380 |
| 5 | JController->execute() | JROOT/components/com_easyblog/easyblog.php:43 |
| 6 | EasyBlogController->display() | JROOT/libraries/joomla/application/component/controller.php:761 |
| 7 | EasyBlogViewBlogger->listings() | JROOT/components/com_easyblog/controllers/controller.php:107 |
| 8 | EB::setMeta() | JROOT/components/com_easyblog/views/blogger/view.html.php:220 |
| 9 | JTable->load() | JROOT/administrator/components/com_easyblog/includes/easyblog.php:2263 |
⇒{"__default":{"session":{"counter":1,"timer":{"start":1757776089,"last":1757776089,"now":1757776089},"client":{"forwarded":"10.3.38.46"},"token":"bdecdbf9b0311a1982d525f6f5b3080e"},"registry":{},"user":{"id":0,"name":null,"username":null,"email":null,"password":null,"password_clear":"","usertype":null,"block":null,"sendEmail":0,"registerDate":null,"lastvisitDate":null,"activation":null,"params":null,"groups":[],"guest":1,"lastResetTime":null,"resetCount":null,"aid":0}},"__easyblog":{"site":{"messages":null}}}
21.35 MB (22,386,720 Bytes)
165 Queries Logged
SELECT `data`
FROM `p3sae_session`
WHERE `session_id` = 'b092759dd4ca95a2cdd2ff0b89ec262d'DELETE
FROM `p3sae_session`
WHERE `time` < '1757767089'SELECT `session_id`
FROM `p3sae_session`
WHERE `session_id` = 'b092759dd4ca95a2cdd2ff0b89ec262d'
LIMIT 0, 1INSERT INTO `p3sae_session`
(`session_id`, `client_id`, `time`)
VALUES
('b092759dd4ca95a2cdd2ff0b89ec262d', 0, '1757776089')SELECT extension_id AS id, element AS "option", params, enabled
FROM p3sae_extensions
WHERE `type` = 'component'
AND `element` = 'com_users'SELECT b.id
FROM p3sae_usergroups AS a
LEFT JOIN p3sae_usergroups AS b
ON b.lft <= a.lft
AND b.rgt >= a.rgt
WHERE a.id = 1SELECT id, rules
FROM `p3sae_viewlevels`SELECT folder AS type, element AS name, params
FROM p3sae_extensions
WHERE enabled >= 1
AND type ='plugin'
AND state >= 0
AND access IN (1,1)
ORDER BY orderingSELECT extension_id AS id, element AS "option", params, enabled
FROM p3sae_extensions
WHERE `type` = 'component'
AND `element` = 'com_languages'SELECT `query`
FROM `p3sae_admintools_wafexceptions`
WHERE (`option` IS NULL OR `option` = '')
AND (`view` IS NULL OR `view` = '')
GROUP BY `query`
ORDER BY `query` ASCSELECT `value`
FROM `p3sae_admintools_storage`
WHERE `key` = 'cparams'SELECT *
FROM `p3sae_admintools_ipautoban`
WHERE `ip` = '10.3.38.46'SELECT `source`,`keepurlparams`
FROM `p3sae_admintools_redirects`
WHERE ((`dest` = 'index.php/blog/authors/j-reilly-infradapt-com') OR (`dest` = 'index.php/blog/authors/j-reilly-infradapt-com?start=715') OR ('index.php/blog/authors/j-reilly-infradapt-com?start=715' LIKE `dest`))
AND `published` = '1'
ORDER BY `ordering` DESC
LIMIT 0, 1SELECT m.id, m.menutype, m.title, m.alias, m.note, m.path AS route, m.link, m.type, m.level, m.language,m.browserNav, m.access, m.params, m.home, m.img, m.template_style_id, m.component_id, m.parent_id,e.element as component
FROM p3sae_menu AS m
LEFT JOIN p3sae_extensions AS e
ON m.component_id = e.extension_id
WHERE m.published = 1
AND m.parent_id > 0
AND m.client_id = 0
ORDER BY m.lftSELECT *
FROM p3sae_easyblog_configs
WHERE `name` = 'config'SELECT `id`
FROM `p3sae_easyblog_users`
WHERE `permalink`='j-reilly-infradapt-com'SELECT extension_id AS id, element AS "option", params, enabled
FROM p3sae_extensions
WHERE `type` = 'component'
AND `element` = 'com_rereplacer'SELECT extension_id AS id, element AS "option", params, enabled
FROM p3sae_extensions
WHERE `type` = 'component'
AND `element` = 'com_easyblog'SELECT *
FROM p3sae_languages
WHERE published=1
ORDER BY ordering ASCSELECT id, home, template, s.params
FROM p3sae_template_styles as s
LEFT JOIN p3sae_extensions as e
ON e.element=s.template
AND e.type='template'
AND e.client_id=s.client_id
WHERE s.client_id = 0
AND e.enabled = 1DELETE
FROM `p3sae_easyblog_mailq`
WHERE `status`='1'
AND DATEDIFF(NOW(), `created`) >='7'SELECT `id`
FROM `p3sae_easyblog_mailq`
WHERE `status`='0'
ORDER BY `created` ASC
LIMIT 5SELECT *
FROM `p3sae_easyblog_post`
WHERE `publish_up`<='2025-09-13 15:08:09'
AND `published`='2'
AND `state`='0'
ORDER BY `id`
LIMIT 5SELECT id, created_by
FROM`p3sae_easyblog_post`
WHERE `publish_down` > `publish_up`
AND `publish_down` <= '2025-09-13 15:08:09'
AND `publish_down` != '0000-00-00 00:00:00'
AND `published` = '1'
AND `state` = '0'SELECT *
FROM `p3sae_easyblog_uploader_tmp`
WHERE `created` <= DATE_SUB('2025-09-13 15:08:09' , INTERVAL 120 MINUTE)delete a, b
from `p3sae_easyblog_post` as a
inner join `p3sae_easyblog_revisions` as b
on a.`id` = b.`post_id`
where a.`published` = '9'
and a.`created` <= DATE_SUB('2025-09-13 15:08:09', INTERVAL 3 DAY)SELECT *
FROM `p3sae_menu`
WHERE `published`='1'
AND `link` LIKE 'index.php?option=com_easyblog%'SELECT *
FROM `p3sae_easyblog_acl`
WHERE `published`='1'
ORDER BY `id` ASCSELECT *
FROM `p3sae_easyblog_acl_group`
WHERE `content_id`='1'
AND `type`='
group'SELECT a.rules
FROM p3sae_assets AS a
WHERE (a.id = 1)
GROUP BY a.id, a.rules, a.lftSHOW FULL COLUMNS
FROM `p3sae_assets`SELECT id
FROM p3sae_assets
WHERE parent_id = 0SELECT b.rules
FROM p3sae_assets AS a
LEFT JOIN p3sae_assets AS b
ON b.lft <= a.lft
AND b.rgt >= a.rgt
WHERE (a.id = 1)
GROUP BY b.id, b.rules, b.lft
ORDER BY b.lftselect u.*, e.`id` as `eb_id`, e.`nickname`, e.`avatar`, e.`description`, e.`url`, e.`params` as `eb_params`, e.`published` as `eb_published`, e.`title` as `eb_title`, e.`biography`, e.`permalink`, e.`custom_css`
from `p3sae_users` as u
left join `p3sae_easyblog_users` as e
ON u.`id` = e.`id`
where u.`id` = 295SHOW FULL COLUMNS
FROM `p3sae_users`SELECT *
FROM `p3sae_users`
WHERE `id` = 295SELECT `g`.`id`,`g`.`title`
FROM `p3sae_usergroups` AS g
INNER JOIN `p3sae_user_usergroup_map` AS m
ON m.group_id = g.id
WHERE `m`.`user_id` = 295SELECT `group_id`
FROM `p3sae_user_usergroup_map`
WHERE `user_id` = '295'SELECT *
FROM `p3sae_easyblog_acl_group`
WHERE `content_id` IN (2, 3)
AND `type`='
group'SELECT *
FROM p3sae_easyblog_meta
WHERE `content_id` = '295'
AND `type` = 'blogger'SELECT *
FROM p3sae_easyblog_users
WHERE `id` = '295'SELECT SQL_CALC_FOUND_ROWS a.`id` AS key1, a.*, ifnull(f.`id`, 0) as `featured`
FROM `p3sae_easyblog_post` AS a
LEFT JOIN `p3sae_easyblog_featured` AS f
ON a.`id` = f.`content_id`
AND f.`type` = 'post'
WHERE a.`published`='1'
AND a.`state`='0'
AND a.`access` = '0'
AND a.`created_by` = '295'
AND (1 <= (select count(1)
from `p3sae_easyblog_post_category` AS acp
INNER JOIN `p3sae_easyblog_category` as cat
on acp.`category_id` = cat.`id`
where acp.`post_id` = a.`id`
and ( ( cat.`private` = 0 ) OR ( (cat.`private` = 1)
and (0 > 0) ) OR ( (cat.`private` = 2)
and ( (select count(1)
from `p3sae_easyblog_category_acl` as cacl
where cacl.`category_id` = cat.id
and cacl.`acl_id` = 1
and cacl.`content_id` in (1)) > 0 ) ) ) ))
AND ( (a.`source_type` = 'easyblog.sitewide') )
ORDER BY a.`created` desc
LIMIT 715,5select FOUND_ROWS()SELECT COUNT(1) as `voted`, `uid`
FROM `p3sae_easyblog_ratings`
WHERE `uid` IN (157,156,155,154,153)
AND `type`='entry'
AND `created_by`='0'
AND (`sessionid` = 'b092759dd4ca95a2cdd2ff0b89ec262d' OR `ip` = '10.3.38.46')
GROUP BY `uid`
ORDER BY NULLSELECT AVG(`value`) AS `ratings` ,COUNT(1) AS `total` ,`uid`
FROM `p3sae_easyblog_ratings` AS a
WHERE a.`uid` IN(157,156,155,154,153)
AND `type`='entry'
GROUP BY `uid`
ORDER BY NULLSELECT a.*
FROM `p3sae_easyblog_comment` AS a
WHERE a.`post_id` IN(157,156,155,154,153)
AND a.`published`='1'SELECT a.`post_id`, COUNT(1) AS `count`
FROM `p3sae_easyblog_comment` AS a
WHERE a.`post_id` IN(157,156,155,154,153)
AND a.`published`='1'
GROUP BY a.`post_id`select a.*, b.`post_id`, b.`primary`
from `p3sae_easyblog_category` as a
inner join `p3sae_easyblog_post_category` as b
on a.`id` = b.`category_id`
where b.`post_id` IN ( 157,156,155,154,153)select a.*, b.`post_id`
from `p3sae_easyblog_tag` as a
inner join `p3sae_easyblog_post_tag` as b
on a.`id` = b.`tag_id`
where b.`post_id` IN ( 157,156,155,154,153)select a.*
from `p3sae_easyblog_revisions` as a
where a.`id` IN ( 299,175,445,306,282)select `a`.`id` as `cat_fg_id`, `a`.`category_id` as `cat_fg_category_id`, `a`.`group_id` as `cat_fg_group_id`, `fg`.`id` as `fg_id`, `fg`.`title` as `fg_title`, `fg`.`description` as `fg_description`, `fg`.`created` as `fg_created`, `fg`.`state` as `fg_state`, `fg`.`read` as `fg_read`, `fg`.`write` as `fg_write`, `fg`.`params` as `fg_params`, `f`.`id` as `f_id`, `f`.`group_id` as `f_group_id`, `f`.`title` as `f_title`, `f`.`help` as `f_help`, `f`.`state` as `f_state`, `f`.`required` as `f_required`, `f`.`type` as `f_type`, `f`.`params` as `f_params`, `f`.`created` as `f_created`, `f`.`options` as `f_options`, `fv`.`id` as `fv_id`, `fv`.`field_id` as `fv_field_id`, `fv`.`post_id` as `fv_post_id`, `fv`.`value` as `fv_value`
from `p3sae_easyblog_category_fields_groups` as a
inner join `p3sae_easyblog_post_category` as p
on `a`.`category_id` = `p`.`category_id`
inner join `p3sae_easyblog_fields_groups` as fg
on `a`.`group_id` = `fg`.`id`
inner join `p3sae_easyblog_fields` as f
on `fg`.`id` = `f`.`group_id`
left join `p3sae_easyblog_fields_values` as fv
on `fv`.`field_id` = `f`.`id`
and `fv`.`post_id` = `p`.`post_id`
where p.post_id IN (157,156,155,154,153)select *
from `p3sae_easyblog_meta`
where `content_id` in (157,156,155,154,153)
and `type` = 'post'SELECT `group_id`
FROM `p3sae_easyblog_category_fields_groups`
WHERE `category_id`='9'SELECT a.*
FROM `p3sae_easyblog_fields` AS a
INNER JOIN `p3sae_easyblog_category_fields_groups` AS b
ON a.`group_id`= b.`group_id`
WHERE b.`category_id`='9'
AND a.`state`='1'
ORDER BY a.`created` DESCSELECT `group_id`
FROM `p3sae_easyblog_category_fields_groups`
WHERE `category_id`='11'SELECT a.*
FROM `p3sae_easyblog_fields` AS a
INNER JOIN `p3sae_easyblog_category_fields_groups` AS b
ON a.`group_id`= b.`group_id`
WHERE b.`category_id`='11'
AND a.`state`='1'
ORDER BY a.`created` DESCSELECT `group_id`
FROM `p3sae_easyblog_category_fields_groups`
WHERE `category_id`='12'SELECT a.*
FROM `p3sae_easyblog_fields` AS a
INNER JOIN `p3sae_easyblog_category_fields_groups` AS b
ON a.`group_id`= b.`group_id`
WHERE b.`category_id`='12'
AND a.`state`='1'
ORDER BY a.`created` DESCselect `id`
FROM `p3sae_easyblog_feedburner`
where userid = '295'SELECT *
FROM p3sae_easyblog_feedburner
WHERE `id` = '2'SELECT `id`
FROM `p3sae_easyblog_subscriptions`
WHERE `uid` = '295'
AND `utype` = 'blogger'
AND `email` = ''SELECT id
FROM p3sae_assets
WHERE parent_id = 0SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT id
FROM p3sae_assets
WHERE parent_id = 0SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT COUNT(1)
FROM `p3sae_easyblog_featured`
WHERE `content_id`='295'
AND `type`='blogger'SELECT *
FROM `p3sae_easyblog_oauth`
WHERE `user_id`='295'
AND `type`='twitter'
LIMIT 1SELECT id
FROM p3sae_assets
WHERE parent_id = 0SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT id
FROM p3sae_assets
WHERE parent_id = 0SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT r.*
FROM p3sae_rereplacer AS r
WHERE r.published = 1
AND (r.area = 'articles')
ORDER BY r.ordering, r.idSELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT *
FROM p3sae_easyblog_tag
WHERE `id` = '76'SELECT *
FROM p3sae_easyblog_tag
WHERE `id` = '55'SELECT *
FROM p3sae_easyblog_tag
WHERE `id` = '143'SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT a.*
FROM `p3sae_easyblog_comment` a
INNER JOIN p3sae_users AS c
ON a.`created_by` = c.`id`
WHERE a.`post_id` = '157'
AND a.`published` = 1
ORDER BY a.`lft` asc
LIMIT 3SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT id
FROM p3sae_assets
WHERE parent_id = 0SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT id
FROM p3sae_assets
WHERE parent_id = 0SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT *
FROM p3sae_easyblog_tag
WHERE `id` = '142'SELECT *
FROM p3sae_easyblog_tag
WHERE `id` = '21'SELECT *
FROM p3sae_easyblog_tag
WHERE `id` = '115'SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT a.*
FROM `p3sae_easyblog_comment` a
INNER JOIN p3sae_users AS c
ON a.`created_by` = c.`id`
WHERE a.`post_id` = '156'
AND a.`published` = 1
ORDER BY a.`lft` asc
LIMIT 3SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT id
FROM p3sae_assets
WHERE parent_id = 0SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT id
FROM p3sae_assets
WHERE parent_id = 0SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT *
FROM p3sae_easyblog_tag
WHERE `id` = '106'SELECT *
FROM p3sae_easyblog_tag
WHERE `id` = '34'SELECT *
FROM p3sae_easyblog_tag
WHERE `id` = '141'SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT a.*
FROM `p3sae_easyblog_comment` a
INNER JOIN p3sae_users AS c
ON a.`created_by` = c.`id`
WHERE a.`post_id` = '155'
AND a.`published` = 1
ORDER BY a.`lft` asc
LIMIT 3SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT id
FROM p3sae_assets
WHERE parent_id = 0SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT id
FROM p3sae_assets
WHERE parent_id = 0SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT *
FROM p3sae_easyblog_tag
WHERE `id` = '134'SELECT *
FROM p3sae_easyblog_tag
WHERE `id` = '140'SELECT *
FROM p3sae_easyblog_tag
WHERE `id` = '48'SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT a.*
FROM `p3sae_easyblog_comment` a
INNER JOIN p3sae_users AS c
ON a.`created_by` = c.`id`
WHERE a.`post_id` = '154'
AND a.`published` = 1
ORDER BY a.`lft` asc
LIMIT 3SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT id
FROM p3sae_assets
WHERE parent_id = 0SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT id
FROM p3sae_assets
WHERE parent_id = 0SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT *
FROM p3sae_easyblog_tag
WHERE `id` = '46'SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT a.*
FROM `p3sae_easyblog_comment` a
INNER JOIN p3sae_users AS c
ON a.`created_by` = c.`id`
WHERE a.`post_id` = '153'
AND a.`published` = 1
ORDER BY a.`lft` asc
LIMIT 3SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT m.id, m.title, m.module, m.position, m.content, m.showtitle, m.params, mm.menuid
FROM p3sae_modules AS m
LEFT JOIN p3sae_modules_menu AS mm
ON mm.moduleid = m.id
LEFT JOIN p3sae_extensions AS e
ON e.element = m.module
AND e.client_id = m.client_id
WHERE m.published = 1
AND e.enabled = 1
AND (m.publish_up = '0000-00-00 00:00:00' OR m.publish_up <= '2025-09-13 15:08:09')
AND (m.publish_down = '0000-00-00 00:00:00' OR m.publish_down >= '2025-09-13 15:08:09')
AND m.access IN (1,1)
AND m.client_id = 0
AND (mm.menuid = 155 OR mm.menuid <= 0)
ORDER BY m.position, m.orderingSELECT id
FROM p3sae_assets
WHERE parent_id = 0SELECT id
FROM p3sae_assets
WHERE parent_id = 0SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT id
FROM p3sae_assets
WHERE parent_id = 0SELECT id
FROM p3sae_assets
WHERE parent_id = 0SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT `template`
FROM `p3sae_template_styles`
WHERE `home`='1'
AND `client_id`='0'SELECT r.*
FROM p3sae_rereplacer AS r
WHERE r.published = 1
AND (r.area = 'component')
ORDER BY r.ordering, r.idSELECT r.*
FROM p3sae_rereplacer AS r
WHERE r.published = 1
AND (r.area = 'body')
ORDER BY r.ordering, r.idSELECT r.*
FROM p3sae_rereplacer AS r
WHERE r.published = 1
AND (r.area = 'everywhere')
ORDER BY r.ordering, r.idUPDATE `p3sae_session`
SET `data` = 'joomla|s:1480:\"Tzo5OiJKUmVnaXN0cnkiOjE6e3M6NzoiACoAZGF0YSI7Tzo4OiJzdGRDbGFzcyI6Mjp7czo5OiJfX2RlZmF1bHQiO086ODoic3RkQ2xhc3MiOjM6e3M6Nzoic2Vzc2lvbiI7Tzo4OiJzdGRDbGFzcyI6NDp7czo3OiJjb3VudGVyIjtpOjE7czo1OiJ0aW1lciI7Tzo4OiJzdGRDbGFzcyI6Mzp7czo1OiJzdGFydCI7aToxNzU3Nzc2MDg5O3M6NDoibGFzdCI7aToxNzU3Nzc2MDg5O3M6Mzoibm93IjtpOjE3NTc3NzYwODk7fXM6NjoiY2xpZW50IjtPOjg6InN0ZENsYXNzIjoxOntzOjk6ImZvcndhcmRlZCI7czoxMDoiMTAuMy4zOC40NiI7fXM6NToidG9rZW4iO3M6MzI6ImJkZWNkYmY5YjAzMTFhMTk4MmQ1MjVmNmY1YjMwODBlIjt9czo4OiJyZWdpc3RyeSI7Tzo5OiJKUmVnaXN0cnkiOjE6e3M6NzoiACoAZGF0YSI7Tzo4OiJzdGRDbGFzcyI6MDp7fX1zOjQ6InVzZXIiO086NToiSlVzZXIiOjI1OntzOjk6IgAqAGlzUm9vdCI7YjowO3M6MjoiaWQiO2k6MDtzOjQ6Im5hbWUiO047czo4OiJ1c2VybmFtZSI7TjtzOjU6ImVtYWlsIjtOO3M6ODoicGFzc3dvcmQiO047czoxNDoicGFzc3dvcmRfY2xlYXIiO3M6MDoiIjtzOjg6InVzZXJ0eXBlIjtOO3M6NToiYmxvY2siO047czo5OiJzZW5kRW1haWwiO2k6MDtzOjEyOiJyZWdpc3RlckRhdGUiO047czoxMzoibGFzdHZpc2l0RGF0ZSI7TjtzOjEwOiJhY3RpdmF0aW9uIjtOO3M6NjoicGFyYW1zIjtOO3M6NjoiZ3JvdXBzIjthOjA6e31zOjU6Imd1ZXN0IjtpOjE7czoxMzoibGFzdFJlc2V0VGltZSI7TjtzOjEwOiJyZXNldENvdW50IjtOO3M6MTA6IgAqAF9wYXJhbXMiO086OToiSlJlZ2lzdHJ5IjoxOntzOjc6IgAqAGRhdGEiO086ODoic3RkQ2xhc3MiOjA6e319czoxNDoiACoAX2F1dGhHcm91cHMiO2E6MTp7aTowO2k6MTt9czoxNDoiACoAX2F1dGhMZXZlbHMiO2E6Mjp7aTowO2k6MTtpOjE7aToxO31zOjE1OiIAKgBfYXV0aEFjdGlvbnMiO047czoxMjoiACoAX2Vycm9yTXNnIjtOO3M6MTA6IgAqAF9lcnJvcnMiO2E6MDp7fXM6MzoiYWlkIjtpOjA7fX1zOjEwOiJfX2Vhc3libG9nIjtPOjg6InN0ZENsYXNzIjoxOntzOjQ6InNpdGUiO086ODoic3RkQ2xhc3MiOjE6e3M6ODoibWVzc2FnZXMiO047fX19fQ==\";'
, `time` = '1757776089'
WHERE `session_id` = 'b092759dd4ca95a2cdd2ff0b89ec262d'
61 Query Types Logged, Sorted by Occurrences.
SELECT Tables:
62 × SELECT `template`
FROM `p3sae_template_styles`17 × SELECT id
FROM p3sae_assets13 × SELECT *
FROM p3sae_easyblog_tag5 × SELECT a.*
FROM `p3sae_easyblog_comment` a
INNER JOIN p3sae_users AS c
ON a.`created_by` = c.`id`4 × SELECT extension_id AS id, element AS "option", params, enabled
FROM p3sae_extensions4 × SELECT r.*
FROM p3sae_rereplacer AS r3 × SELECT a.*
FROM `p3sae_easyblog_fields` AS a
INNER JOIN `p3sae_easyblog_category_fields_groups` AS b
ON a.`group_id`= b.`group_id`3 × SELECT `group_id`
FROM `p3sae_easyblog_category_fields_groups`2 × SELECT *
FROM `p3sae_easyblog_acl_group`1 × SELECT AVG(`value`) AS `ratings` ,COUNT(1) AS `total` ,`uid`
FROM `p3sae_easyblog_ratings` AS a1 × SELECT a.*
FROM `p3sae_easyblog_comment` AS a1 × SELECT a.`post_id`, COUNT(1) AS `count`
FROM `p3sae_easyblog_comment` AS a1 × SELECT m.id, m.title, m.module, m.position, m.content, m.showtitle, m.params, mm.menuid
FROM p3sae_modules AS m
LEFT JOIN p3sae_modules_menu AS mm
ON mm.moduleid = m.id
LEFT JOIN p3sae_extensions AS e
ON e.element = m.module
AND e.client_id = m.client_id1 × SELECT COUNT(1) as `voted`, `uid`
FROM `p3sae_easyblog_ratings`1 × SELECT *
FROM p3sae_easyblog_users1 × SELECT SQL_CALC_FOUND_ROWS a.`id` AS key1, a.*, ifnull(f.`id`, 0) as `featured`
FROM `p3sae_easyblog_post` AS a
LEFT JOIN `p3sae_easyblog_featured` AS f
ON a.`id` = f.`content_id`
AND f.`type` = 'post'1 × select FOUND_ROWS(1 × select a.*, b.`post_id`, b.`primary`
from `p3sae_easyblog_category` as a
inner join `p3sae_easyblog_post_category` as b
on a.`id` = b.`category_id`1 × select a.*, b.`post_id`
from `p3sae_easyblog_tag` as a
inner join `p3sae_easyblog_post_tag` as b
on a.`id` = b.`tag_id`1 × select `id`
FROM `p3sae_easyblog_feedburner`1 × SELECT *
FROM p3sae_easyblog_feedburner1 × SELECT `id`
FROM `p3sae_easyblog_subscriptions`1 × SELECT *
FROM `p3sae_easyblog_oauth`1 × SELECT *
FROM p3sae_easyblog_meta1 × select a.*
from `p3sae_easyblog_revisions` as a1 × select `a`.`id` as `cat_fg_id`, `a`.`category_id` as `cat_fg_category_id`, `a`.`group_id` as `cat_fg_group_id`, `fg`.`id` as `fg_id`, `fg`.`title` as `fg_title`, `fg`.`description` as `fg_description`, `fg`.`created` as `fg_created`, `fg`.`state` as `fg_state`, `fg`.`read` as `fg_read`, `fg`.`write` as `fg_write`, `fg`.`params` as `fg_params`, `f`.`id` as `f_id`, `f`.`group_id` as `f_group_id`, `f`.`title` as `f_title`, `f`.`help` as `f_help`, `f`.`state` as `f_state`, `f`.`required` as `f_required`, `f`.`type` as `f_type`, `f`.`params` as `f_params`, `f`.`created` as `f_created`, `f`.`options` as `f_options`, `fv`.`id` as `fv_id`, `fv`.`field_id` as `fv_field_id`, `fv`.`post_id` as `fv_post_id`, `fv`.`value` as `fv_value`
from `p3sae_easyblog_category_fields_groups` as a
inner join `p3sae_easyblog_post_category` as p
on `a`.`category_id` = `p`.`category_id`
inner join `p3sae_easyblog_fields_groups` as fg
on `a`.`group_id` = `fg`.`id`
inner join `p3sae_easyblog_fields` as f
on `fg`.`id` = `f`.`group_id`
left join `p3sae_easyblog_fields_values` as fv
on `fv`.`field_id` = `f`.`id`
and `fv`.`post_id` = `p`.`post_id`1 × select *
from `p3sae_easyblog_meta`1 × SELECT COUNT(1)
FROM `p3sae_easyblog_featured`1 × SELECT *
FROM `p3sae_users`1 × SELECT `source`,`keepurlparams`
FROM `p3sae_admintools_redirects`1 × SELECT *
FROM `p3sae_admintools_ipautoban`1 × SELECT m.id, m.menutype, m.title, m.alias, m.note, m.path AS route, m.link, m.type, m.level, m.language,m.browserNav, m.access, m.params, m.home, m.img, m.template_style_id, m.component_id, m.parent_id,e.element as component
FROM p3sae_menu AS m
LEFT JOIN p3sae_extensions AS e
ON m.component_id = e.extension_id1 × SELECT *
FROM p3sae_easyblog_configs1 × SELECT `id`
FROM `p3sae_easyblog_users`1 × SELECT `value`
FROM `p3sae_admintools_storage`1 × SELECT `query`
FROM `p3sae_admintools_wafexceptions`1 × SELECT `session_id`
FROM `p3sae_session`1 × SELECT b.id
FROM p3sae_usergroups AS a
LEFT JOIN p3sae_usergroups AS b
ON b.lft <= a.lft
AND b.rgt >= a.rgt1 × SELECT id, rules
FROM `p3sae_viewlevels1 × SELECT folder AS type, element AS name, params
FROM p3sae_extensions1 × SELECT *
FROM p3sae_languages1 × SELECT id, home, template, s.params
FROM p3sae_template_styles as s
LEFT JOIN p3sae_extensions as e
ON e.element=s.template
AND e.type='template'
AND e.client_id=s.client_id1 × SELECT b.rules
FROM p3sae_assets AS a
LEFT JOIN p3sae_assets AS b
ON b.lft <= a.lft
AND b.rgt >= a.rgt1 × SELECT a.rules
FROM p3sae_assets AS a1 × select u.*, e.`id` as `eb_id`, e.`nickname`, e.`avatar`, e.`description`, e.`url`, e.`params` as `eb_params`, e.`published` as `eb_published`, e.`title` as `eb_title`, e.`biography`, e.`permalink`, e.`custom_css`
from `p3sae_users` as u
left join `p3sae_easyblog_users` as e
ON u.`id` = e.`id`1 × SELECT `data`
FROM `p3sae_session`1 × SELECT `g`.`id`,`g`.`title`
FROM `p3sae_usergroups` AS g
INNER JOIN `p3sae_user_usergroup_map` AS m
ON m.group_id = g.id1 × SELECT *
FROM `p3sae_easyblog_acl`1 × SELECT *
FROM `p3sae_menu`1 × SELECT `id`
FROM `p3sae_easyblog_mailq`1 × SELECT *
FROM `p3sae_easyblog_post`1 × SELECT id, created_by
FROM`p3sae_easyblog_post`1 × SELECT *
FROM `p3sae_easyblog_uploader_tmp`1 × SELECT `group_id`
FROM `p3sae_user_usergroup_map`
OTHER Tables:
1 × SHOW FULL COLUMNS
FROM `p3sae_users1 × UPDATE `p3sae_session`
SET `data` = 'joomla|s:1480:\"Tzo5OiJKUmVnaXN0cnkiOjE6e3M6NzoiACoAZGF0YSI7Tzo4OiJzdGRDbGFzcyI6Mjp7czo5OiJfX2RlZmF1bHQiO086ODoic3RkQ2xhc3MiOjM6e3M6Nzoic2Vzc2lvbiI7Tzo4OiJzdGRDbGFzcyI6NDp7czo3OiJjb3VudGVyIjtpOjE7czo1OiJ0aW1lciI7Tzo4OiJzdGRDbGFzcyI6Mzp7czo1OiJzdGFydCI7aToxNzU3Nzc2MDg5O3M6NDoibGFzdCI7aToxNzU3Nzc2MDg5O3M6Mzoibm93IjtpOjE3NTc3NzYwODk7fXM6NjoiY2xpZW50IjtPOjg6InN0ZENsYXNzIjoxOntzOjk6ImZvcndhcmRlZCI7czoxMDoiMTAuMy4zOC40NiI7fXM6NToidG9rZW4iO3M6MzI6ImJkZWNkYmY5YjAzMTFhMTk4MmQ1MjVmNmY1YjMwODBlIjt9czo4OiJyZWdpc3RyeSI7Tzo5OiJKUmVnaXN0cnkiOjE6e3M6NzoiACoAZGF0YSI7Tzo4OiJzdGRDbGFzcyI6MDp7fX1zOjQ6InVzZXIiO086NToiSlVzZXIiOjI1OntzOjk6IgAqAGlzUm9vdCI7YjowO3M6MjoiaWQiO2k6MDtzOjQ6Im5hbWUiO047czo4OiJ1c2VybmFtZSI7TjtzOjU6ImVtYWlsIjtOO3M6ODoicGFzc3dvcmQiO047czoxNDoicGFzc3dvcmRfY2xlYXIiO3M6MDoiIjtzOjg6InVzZXJ0eXBlIjtOO3M6NToiYmxvY2siO047czo5OiJzZW5kRW1haWwiO2k6MDtzOjEyOiJyZWdpc3RlckRhdGUiO047czoxMzoibGFzdHZpc2l0RGF0ZSI7TjtzOjEwOiJhY3RpdmF0aW9uIjtOO3M6NjoicGFyYW1zIjtOO3M6NjoiZ3JvdXBzIjthOjA6e31zOjU6Imd1ZXN0IjtpOjE7czoxMzoibGFzdFJlc2V0VGltZSI7TjtzOjEwOiJyZXNldENvdW50IjtOO3M6MTA6IgAqAF9wYXJhbXMiO086OToiSlJlZ2lzdHJ5IjoxOntzOjc6IgAqAGRhdGEiO086ODoic3RkQ2xhc3MiOjA6e319czoxNDoiACoAX2F1dGhHcm91cHMiO2E6MTp7aTowO2k6MTt9czoxNDoiACoAX2F1dGhMZXZlbHMiO2E6Mjp7aTowO2k6MTtpOjE7aToxO31zOjE1OiIAKgBfYXV0aEFjdGlvbnMiO047czoxMjoiACoAX2Vycm9yTXNnIjtOO3M6MTA6IgAqAF9lcnJvcnMiO2E6MDp7fXM6MzoiYWlkIjtpOjA7fX1zOjEwOiJfX2Vhc3libG9nIjtPOjg6InN0ZENsYXNzIjoxOntzOjQ6InNpdGUiO086ODoic3RkQ2xhc3MiOjE6e3M6ODoibWVzc2FnZXMiO047fX19fQ==\";' , `time` = '1757776089'1 × SHOW FULL COLUMNS
FROM `p3sae_assets1 × delete a, b
from `p3sae_easyblog_post` as a
inner join `p3sae_easyblog_revisions` as b
on a.`id` = b.`post_id`1 × INSERT INTO `p3sae_session` (`session_id`, `client_id`, `time`)
VALUES ('b092759dd4ca95a2cdd2ff0b89ec262d', 0, '1757776089'1 × DELETE
FROM `p3sae_easyblog_mailq`1 × DELETE
FROM `p3sae_session`
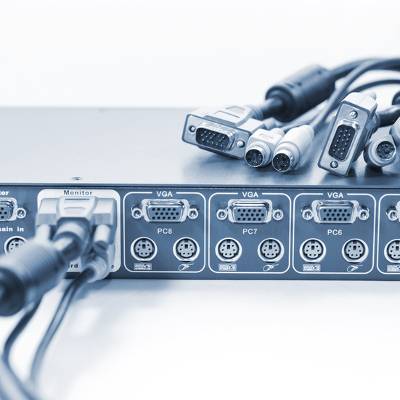 A business's IT infrastructure is complex and confusing. Just like a puzzle, it is made up of several vastly different pieces that come together to perform a particular function. One of the things that ties an IT infrastructure together is a KVM switch. Without a quality KVM switch, your network might fail to operate properly. Here are a few tips to help you choose the right KVM solution for your business.
A business's IT infrastructure is complex and confusing. Just like a puzzle, it is made up of several vastly different pieces that come together to perform a particular function. One of the things that ties an IT infrastructure together is a KVM switch. Without a quality KVM switch, your network might fail to operate properly. Here are a few tips to help you choose the right KVM solution for your business. Microsoft Outlook is a common mail solution for businesses, but it can be tricky to use without utilizing keyboard shortcuts. Just like Microsoft Word, Outlook has several key commands that can be used to jumpstart your productivity and save time, which can be better spent on other activities, like training exercises or more important tasks.
Microsoft Outlook is a common mail solution for businesses, but it can be tricky to use without utilizing keyboard shortcuts. Just like Microsoft Word, Outlook has several key commands that can be used to jumpstart your productivity and save time, which can be better spent on other activities, like training exercises or more important tasks. Naturally, if you saw your lamp levitate, you would believe it to be the work of a ghoul and you would cry out in terror. What then would you believe if you saw your PC’s cursor begin to move on its own? In a spooky scenario like this, your computer isn’t haunted. It’s hacked. In the real world, the latter is the scarier of the two.
Naturally, if you saw your lamp levitate, you would believe it to be the work of a ghoul and you would cry out in terror. What then would you believe if you saw your PC’s cursor begin to move on its own? In a spooky scenario like this, your computer isn’t haunted. It’s hacked. In the real world, the latter is the scarier of the two. Have you ever tried to search for something on Google, only to be disappointed that you couldn't find what you were looking for? You might think you're being extremely specific, but in reality, you're not doing anything different from the average joe. Googling is an art lost to the ages, a secret technique of legend. But, not really. Here are some tips to help you get more out of the world's most popular search engine.
Have you ever tried to search for something on Google, only to be disappointed that you couldn't find what you were looking for? You might think you're being extremely specific, but in reality, you're not doing anything different from the average joe. Googling is an art lost to the ages, a secret technique of legend. But, not really. Here are some tips to help you get more out of the world's most popular search engine. Sometimes it seems like the Internet is plotting against you, and nothing is safe, ever. Even if you don't have any thugs waiting to steal your data, there are hackers - thieves - who will steal it anyway, waiting to take it when you least expect it. One of the most secure ways to protect your company's digital assets is to enact a "zero trust" policy for your network.
Sometimes it seems like the Internet is plotting against you, and nothing is safe, ever. Even if you don't have any thugs waiting to steal your data, there are hackers - thieves - who will steal it anyway, waiting to take it when you least expect it. One of the most secure ways to protect your company's digital assets is to enact a "zero trust" policy for your network.