 As a business owner, you might find yourself on the road a lot, and you likely feel the need to check your email for important updates from the home base. This becomes more difficult as you move from civilization into the vast unknown, with the only available WiFi connections found in public places. Unfortunately, public WiFi spots are notorious for being unsecured and unprotected, and it’s important to practice proper security when dealing with them.
As a business owner, you might find yourself on the road a lot, and you likely feel the need to check your email for important updates from the home base. This becomes more difficult as you move from civilization into the vast unknown, with the only available WiFi connections found in public places. Unfortunately, public WiFi spots are notorious for being unsecured and unprotected, and it’s important to practice proper security when dealing with them.
Staying safe on a public WiFi connection is far more difficult than it sounds. It’s kind of like staying in a seedy motel room on the outskirts of town. Sure, it doesn’t cost you much, but you won’t know if something is wrong until it’s too late. Who knows what dangers could lurk in the cesspools that are public WiFi connections? You might not know what’s out there, but we’ll tell you one thing; you’re not missing out on anything you want to get involved with. Here are some tips to help you keep yourself safe when using public WiFi hotspots.
Turn off File Sharing
One of the easiest ways to secure your device from a hacking attack while on public WiFi is by turning off file sharing. To do this in Windows, follow these steps:
Click on Control Panel, then select Network and Sharing Center.
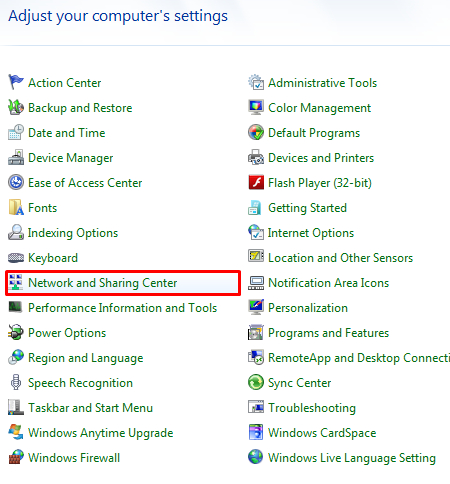
In the left-hand column, click on Change advanced sharing settings.

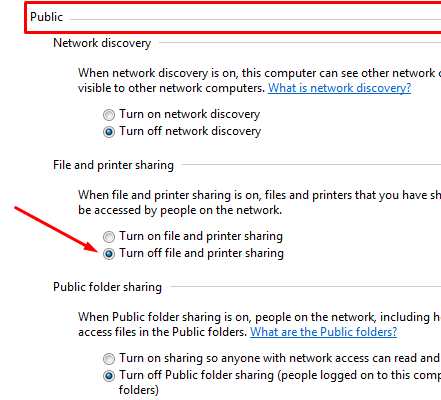
In the public heading, select Turn off file and printer sharing.
Check Security Certificates of Sites
This should go without saying, but unless a site has an up-to-date security certificate, you should always assume the worst. Be wary of entering any information into an unsecured server. You can tell if the site’s security certificate is up-to-date by hovering over the padlock symbol next to the site’s URL.
![]()
If the domain of the website uses the prefix HTTPS, the site should be secured and you can freely enter any information you must.
While you’re at it, you should also make sure that your operating system and all used applications are up-to-date. We know how business is; you get caught up with your day-to-day operations and forget to apply the latest patches and security updates. This can have negative effects on your system’s ability to block threats. Always ensure that your updates are accepted through a secure connection (i.e. one which is familiar and private), and never download updates if they are appearing on a public network. Or, better yet, Infradapt can apply all of the necessary patches to your systems remotely, alleviating you of the stress.
Use a Virtual Private Network from Infradapt
If you want secure browsing wherever your business takes you, your best chance at success is to integrate a Virtual Private Network (VPN) into your mobile business strategy. With a VPN, you can rest easy knowing that you and your institution's authorized users are the only users on the network. This cuts the risk of a potential hacking attack significantly.
With these tips, you’re sure to increase the odds of escaping from a public WiFi nightmare unscathed. For more tips and tricks on how to keep your business productive and efficient, give us a call at 800.394.2301.

