You might use USB every day for your general technology needs, but do you know the difference between the various kinds of USB? This week’s tech term is dedicated to investigating the different types of Universal Serial Bus (USB) ports, including its history, development, and uses.
The Origins of USB
First developed and implemented in 1996, the USB cable was created with the purpose of connecting devices to a computer in mind. A total of seven leaders in the computing and communications industry--Compaq, DEC, IBM, Intel, Microsoft, NEC, and Nortel--wanted to create a simple solution that could allow several different kinds of devices to connect to a PC.
Essentially, an early USB connection provided a data transfer of about 1.5 Mbps to 12 Mps. While this isn’t as fast as today’s standards, it was quite remarkable for the time. The first major release of USB technology was in September 1998, and it provided users with a 12 Mbps transfer rate on high-speed devices. Apple’s own iMac computer was actually one of the first devices to come with USB built into it, and it success played a major role in the commercialization and popularity of USB. The original USB came in two different connector types: type A, or standard USB, and type B, the more squared-off connector.
Innovations of USB
In August of 2000, USB 2.0 was released. The increase in data transfer was substantial at about 280 Mbps. Additionally, the first mini-USB (types A and B) were also developed. Furthermore, USB 2.0 introduced a new integrated battery charging feature, as well as fast data transfer from the emerging smartphone market. USB 3.0, introduced in November 2008, achieved an impressive 5.0 Gbs transfer rate, and the next decade would only further enhance this. September 2017 brought about the Type-C connector and USB 3.2, resulting in a transfer of around 20 Gbps.
USB Type-C
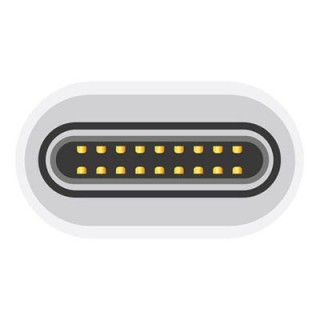
The USB Type-C uses a 24-pin USB connector system. You can identify it by looking for its rotational-symmetrical connector. We think that this is not just the most identifiable feature, but its most important as well. Nowadays, there is no wrong way to plug in your USB cable. In terms of size, the USB-C connector is larger than the micro-B connector. Just like the typical USB wire, one end has a type-A or type-B connection, while the other end has the new type-C connector.
For your reference, here are three of the best new features for USB Type-C:
- It’s designed to be easier to plug in since there is no discernible way that the dongle has to be entered into the device.
- Data transfer and power capability are basically twice what they were with USB 3.1.
- It’s designed to become a future-proof option for data and power transfer for mobile devices.
Unfortunately, not all devices support one cable, but maybe in the future this will become the new standard. For more information about new developments and the latest technology, subscribe to our blog.